 Blog
Blog
How one Retailer Prevented a Repeat Ransomware Attack
ExtraHop
April 14, 2022
"Profit in business comes in repeat customers"
– William Edwards Deming
Ransomware is a highly profitable business. Like any business, they have become adept at innovating and shifting tactics to create demand and keep pace with a changing market. They also value customer retention, which is why 74% of organizations reported multiple ransomware attacks in the past five years, and 80% of organizations that have paid ransom are attacked a second time.
How does ransomware succeed at striking twice? After initially targeting an organization, ransomware gangs often have at least one of several advantages: One option is to return to their initial attack vector, trusting that weak perimeter defenses remain unfortified or that vulnerabilities remain unpatched.
While today's organizations are eager to avoid becoming repeat customers, too many enterprises defend themselves by betting that they can prevent intrusions entirely rather than investing in tools that can beat ransomware at the midgame. This approach leaves security teams without the post-compromise visibility they need to effectively protect their assets from attackers that are already taking residence on network devices.
Another way ransomware actors seize the opportunity to strike twice: By keeping their initial foothold. Should malware-affected devices remain undetected, improperly quarantined, or not fully wiped and restored, the bad actors can linger in an environment, allowing them to restart the process of encrypting and exfiltrating valuable information.
When ransomware remains undetected, slow or incomplete threat response is usually to blame—but the incident response and network forensics is a challenge for many security teams. The process of wading through log files to pinpoint the root cause of an attack and identify impacted systems is incredibly costly and time consuming, even for skilled analysts, which grants attackers the time they need to strike again.
How One Retailer Prevented a Repeat Attack
Last year, a large retailer was a first-time victim of ransomware. The aftermath, like most ransomware attacks, led to financial and reputational damage beyond any extortion payment: Customer data was potentially exposed and access to online services was suspended or delayed leading to lost sales. As an organization, this retailer joins a rapidly growing group of organizations who have suffered damage to their budgets and their bottom lines as a result.
As a first-time victim, the security team knew their risk of being retargeted was high—but convincing their board of directors to incorporate network visibility into their existing security budget delayed the adoption of a network detection and response (NDR) solution. The SUNBURST supply chain attack ultimately jolted leadership into action, leading the company to ExtraHop Reveal(x).
Visibility in the Nick of Time
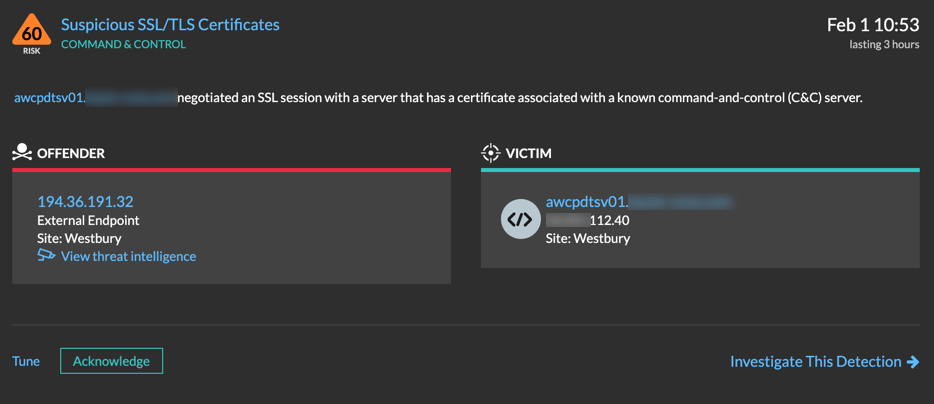
Just a few days after the ExtraHop team installed Reveal(x) on their network, the platform fired a detection for a Suspicious SSL/TLS Certificate associated with command & control activity. After learning that an external endpoint was communicating out of the Netherlands, the retailer's CIO reached out to ExtraHop for assistance.
Detecting Ransomware by Knowing Their Playbook
Command & control (C&C) beaconing is when a malware-infected network device phones home to a malicious external server to ask for further instructions. A compromised device will usually be programmed to send out periodic beacons to maintain contact with the attackers.
While this activity is undoubtedly nefarious, it's also a fairly textbook move for ransomware—which can actually be good news for security teams looking to detect post-compromise activity. As long as defenders know how ransomware typically moves through the network and they have the tools they need to spot that movement, they can regain the advantage by catching and stopping attacks before any damage is done.
Investigating Signs of Malware Infection
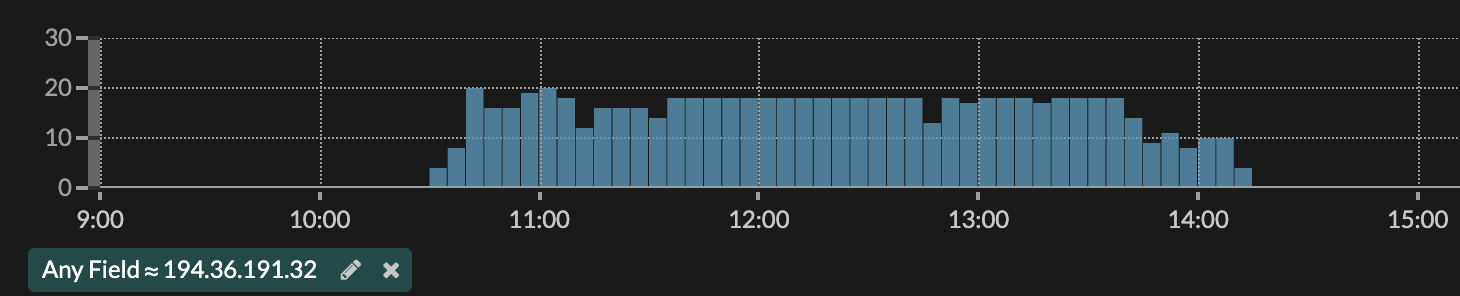
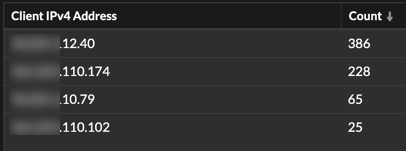
Because the retailer had been hit with ransomware before, it was critical to investigate the extent of the current malware infection. Thanks to the Cloud Record Store feature, the team had indexable data, collected and stored by Reveal(x) since their initial installation. This data could inform the team if anything else on the network was behaving similarly. In Records, they searched for the external IP and grouped by client IP to check for other devices phoning home to the suspicious endpoint.
Reveal(x) showed a total of four hosts reaching out to that endpoint, AKA four infected devices phoning home to a potential attacker.
The customer was able to determine that a common user account was used to access all of these hosts.
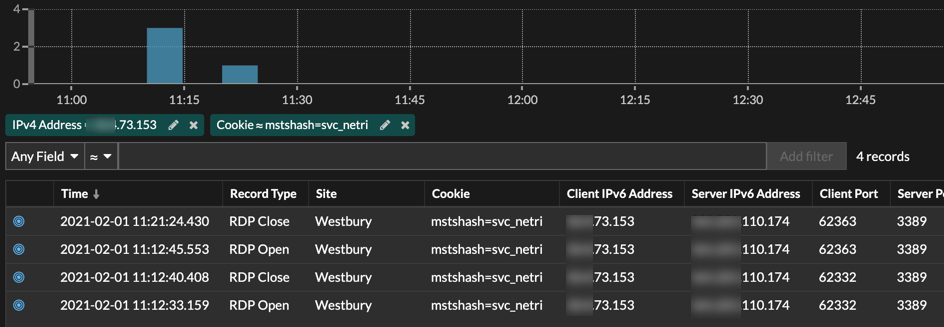
To track any further compromise, the team needed to see if this account was used anywhere else during this time. They checked the records once again, this time for stored Kerberos data, and were able to spot the same four hosts.
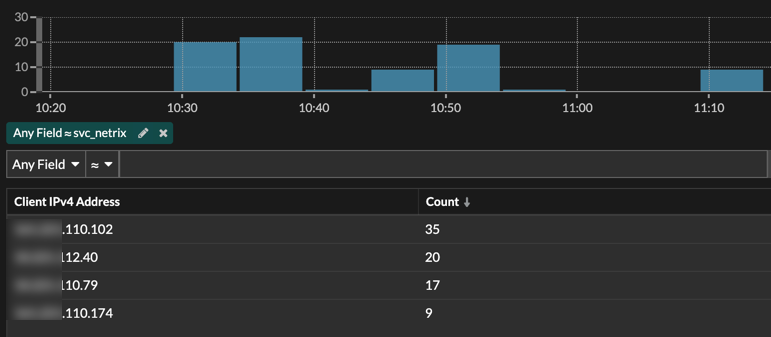
The team then searched Remote Desktop Protocol (RDP) records for that same account and saw that one of the four servers was accessed via RDP from a host in another location, allowing them to pinpoint the origin of the attack.
Stopping Repeat Attacks Post Compromise
The security team immediately contained the device, determining that malware had been lying dormant—most likely from their ransomware attack. Using stored data from ExtraHop Reveal(x), they were able to search through stored and indexed data to track down and contain the compromised host within minutes of reaching out.
Because the adversary had likely maintained its foothold from the initial attack, no amount of additional perimeter security could have prevented a second strike. Thankfully, in this case, the team had the visibility and records they needed to stop and detect the early stages of an attack, allowing them to regain the advantage.
