Detecting RMM Software with ExtraHop
Back to top
January 21, 2025
Detecting RMM Software with ExtraHop
Whether you’re a security analyst or a DIY-er, the right tool for the right job makes life so much easier. Personally, I love power tools–the cordless ones with the interchangeable batteries. But a cordless electric chainsaw is literally a double-edged sword. It not only cuts both ways, but does so with dangerous ease.
For IT and security teams, remote monitoring and management (RMM) software, such as AnyDesk, ConnectWise ScreenConnect, and Splashtop, are a lot like cordless electric chainsaws. On one hand, they make tedious tasks like remote patch installation and troubleshooting far faster and easier. But on the other hand, because they allow remote users such as helpdesk admins to take control of an end user’s computer, threat actors are increasingly exploiting legitimate RMM software to establish an interactive command and control (C2) channel, move laterally across an organization’s network, maintain persistence, and fly under the radar of traditional detection tools by blending in with legitimate operations.
Threat actors may abuse approved RMM software used within the victim’s environment or, once threat actors have control of a compromised device, they may install a legitimate RMM software instance that’s not currently used by the victim organization. Then threat actors will acquire a passcode for the software, which will enable them to interact with the compromised device or leverage software features that install other tools to collect data from the compromised machine.
The Cybersecurity and Infrastructure Security Agency (CISA) issued a warning in 2023 about this growing attack vector, catalogued in the ATT&CK framework as T1219. So it should surprise no one that CrowdStrike reported a 70% increase in adversaries exploiting them in 2024, including Scattered Spider, LockBit, Iran’s Static Kitten, and North Korea’s Famous Chollima.
In keeping with our mission to help organizations reveal cyber risk and build resilience, ExtraHop® has expanded the capabilities of RevealX™, our industry-leading network detection and response (NDR) platform, to identify and detect the use of RMM software across your on-premises and cloud environments (both public and private).
History of RMM Detection in RevealX
RevealX began identifying RMM software passively on the network in 2020 as part of the platform’s automatic asset discovery process. In the same way that RevealX automatically discovers endpoints, their operating systems, cipher suites, and applications by passively watching all the network traffic that endpoints send and receive, RevealX now identifies five top RMM software applications out of the box: ConnectWise ScreenConnect, TeamViewer, Splashtop, AnyDesk, and Atera Agent. We plan to add more automatic identifications in future releases.
Giving RevealX the ability to discover RMM software on the network was just the first step. The next was creating a detector called the New Remote Access Software Activity Detector because it detects devices making a first-time connection to cloud services associated with remote access and remote monitoring and management software. This detector debuted in December 2024, and it gives RevealX the ability to detect and notify the SOC of first-time RMM software usage, so both the activity and the participants can be validated or investigated for potentially malicious use. The combination of automatic discovery and real-time alerts on actual RMM software activity are critical to distinguishing legitimate vs. malicious use of RMM software and to proactively respond.
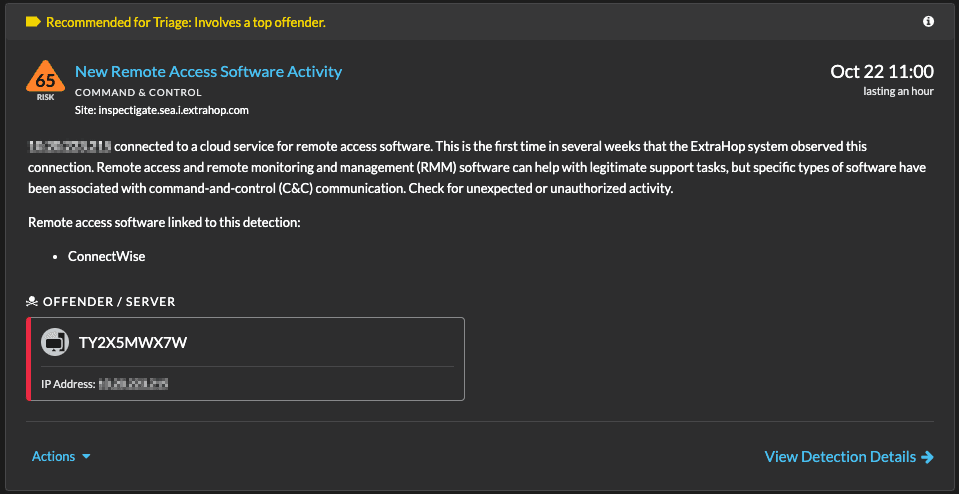
The New Remote Access Software Activity Detector in RevealX helps organizations identify potentially malicious use of RMM software in their environments.
5 Ways to Mitigate RMM Threats
- Proactively block or limit outbound traffic to sites and services associated with remote access software.
- Proactively monitor for devices that are running unauthorized remote access software.
- Proactively implement controls that prevent unauthorized applications from running on devices.
- Quarantine devices making unusual first-time connections to RMM software while checking for indicators of compromise.
- Monitor and investigate unusual activity to minimize potential damage.
RevealX customers can start using the RMM software identification and detection capabilities today.
Not an Extrahop RevealX customer? Explore our online demo to see how RevealX can automatically discover and alert on Remote Access and RMM software activity and address other security use cases.
Discover more

Senior Product Marketing Manager
Adam Foit is a CISSP who began his career in IT Operations in the 1990s. Since then, he as continued to work in the technology industry with a focus on network detection and response, security operations, and network performance management. Adam lives in Knoxville, Tenn. and enjoys hiking and kayaking around the Smoky Mountains with his wife.







