New File-Based Detection and Threat Hunting Capabilities in RevealX Set the Stage for Modern NDR
Back to top
October 16, 2024
New File-Based Detection and Threat Hunting Capabilities in RevealX Set the Stage for Modern NDR
ExtraHop is pleased to announce the release of the latest version of RevealX. This latest release builds off the file hashing and analysis enhancements that ExtraHop announced with its two previous updates and introduces some new breakthrough capabilities. The net result signals a quantum leap in modern network detection and response (NDR) tooling that significantly enhances the security and operations center (SOC) user experience with intuitive file-based detection, investigation and threat hunting capabilities.
File-Based Detection, Investigation and Threat Hunting
Two updates ago, we introduced file hashing and file-type identification for smaller executable files (under 10MB) transferred via HTTP, FTP, and SMB protocols. This add-on was a key step in enabling our customers to gather important file data and laid the groundwork for more advanced file-analysis capabilities.
In our last update, we gave customers more control by allowing them to create custom rules for file hashing, which makes file analysis more precise and efficient. We also operationalized on-demand file carving, enabling users to extract and reassemble packet files directly from network traffic. This capability is critical for forensic investigations.
Additionally, the last update manifested a new integration with CrowdStrike Falcon Adversary Intelligence. In our latest version, we have operationalized a CrowdStrike-enhanced detection feature for IDS users that automatically flags known malicious files, further boosting RevealX’s threat detection capabilities.
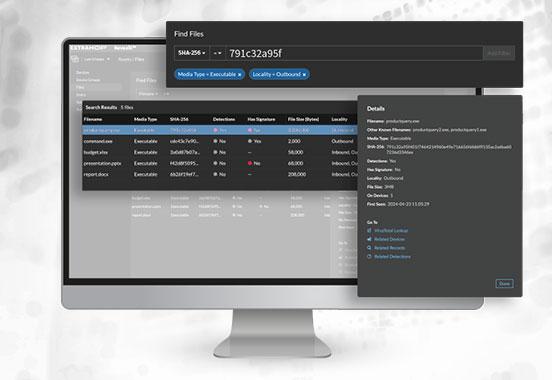
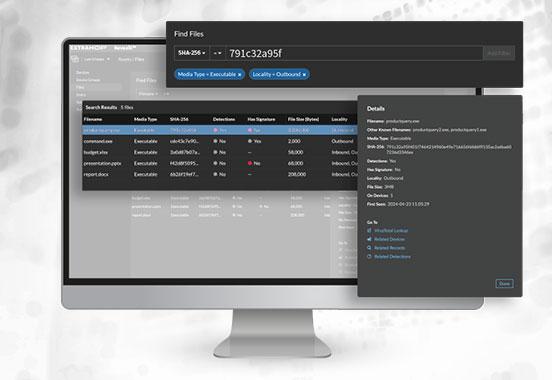
Advancing on the file analysis journey earlier this year, the tool now offers file-based investigation and threat hunting. Notably, this feature includes a comprehensive searchable Files Table, which makes artifact analysis significantly more intuitive and accessible for SOC personnel.
Specifically, this feature provides a centralized console for suspicious file analysis that eliminates the inconvenience of swivel-chair investigations that disrupt SOC efficiencies by forcing analysts to toggle between different applications and screens to probe and contextualize different artifacts. Ultimately, this feature saves SOC teams’ time and energy, enabling them to operate more efficiently and intelligently.

RevealX Files Table
Given the Files Table’s ease of use and end-user navigability, this new RevealX feature promises to significantly transform how analysts investigate suspicious files. The Files Table displays detailed metadata, including SHA256 hash, detection status (for IDS users), file size, the number of devices where the file was observed, and file signed status.

RevealX file-based detections in IDS
Additionally, ExtraHop added a ‘Right-Click File Hash Lookup’ feature that allows analysts to quickly perform file hash lookups and correlations directly from the RevealX platform. This feature also seamlessly integrates with VirusTotal, enabling SOC analysts to immediately verify known malicious files and conduct deeper investigation as needed.
The searchable Files Table in RevealX is a powerful complement to the file hashing, file hash configuration, file carving, and malicious file detection capabilities that ExtraHop introduced over the last year. The benefit of these enhanced file analysis features is that they help plug a significant gap in security coverage. Specifically, they provide organizations with a means to perform file-based detection across unmanaged assets and other endpoints where agents aren’t installed like Internet of Things (IoT) devices, for example.
Empowering full visibility into file content and related metadata helps SOC teams dramatically minimize their mean time to detect and respond (MTTD/R) to malicious payloads and other types of network contamination. This feature is further enriched via integration with CrowdStrike Falcon Adversary Intelligence to help defenders derive granular insight into the precise nature and behavior of malicious files.
Beyond the addition of the Files Table, the latest release also enhances SOC teams’ security controls by introducing a pre-configured password prompt into the File Carving interface. This provision helps SOC teams safeguard their control environments from unintended malware executions by analysts that may inadvertently access unauthorized workflows or artifacts they are not fully familiar with.

RevealX file-carving interface
Taken in concert, the integration of the Files Table with RevealX’s file hashing, file hash configuration, file carving, and malicious file detection capabilities promises transformative benefits for the SOC environment. The end result of RevealX latest product updates is a streamlined workflow that helps SOC analysts save hours of arduous investigation time, while consolidating more of their mission-critical security functions within a single NDR console.
Discover more
ExtraHop is on a mission to arm security teams to confront active threats and stop breaches. Our RevealX™ 360 platform, powered by cloud-scale AI, covertly decrypts and analyzes all cloud and network traffic in real time to eliminate blind spots and detect threats that other tools miss. Sophisticated machine learning models are applied to petabytes of telemetry collected continuously, helping ExtraHop customers to identify suspicious behavior and secure over 15 million IT assets, 2 million POS systems, and 50 million patient records. ExtraHop is a market share leader in network detection and response with 30 recent industry awards including Forbes AI 50, Cybercrime Ransomware 25, and SC Media Security Innovator.
Learn more at our About Us page.