SonicWall Ransomware Warning: Attacks via SRA & SMA Devices
Back to top
July 15, 2021
SonicWall Ransomware Warning: Attacks via SRA & SMA Devices
Back in April 2021, we discussed three SonicWall vulnerabilities affecting the company's Email Security products. Now, an unpatched vulnerability in older versions of the company's SSL VPN firmware for Secure Mobile Access and Secure Remote Access products has created a new critical threat against legacy devices. SonicWall is warning of an "imminent ransomware campaign."
Organizations need to immediately understand what software and devices might be affected and identify vulnerable legacy devices in their environment. This can be remarkably challenging because of the need for an up-to-date device inventory in sprawling environments, let alone detecting software types and versions that devices are running and which need to be addressed.
In this case, discontinued SSL VPN devices are still in operation with known vulnerabilities. These devices are easily found on the internet and cannot be patched because they are out of service. Most likely, these haven't been disabled in these instances because they support a business-critical objective. Ransomware attackers are capitalizing on these facts.
According to our threat research data, .06% of devices being monitored by ExtraHop are potentially impacted by this threat. It only takes one entry point for attackers to land and pivot within an organization.
ExtraHop advises quickly identifying and grouping SonicWall SSL VPN devices for investigation. The faster an organization can identify the vulnerable devices and whether they were compromised, the better the chances of avoiding irrecoverable damage. And the broad benefits of comprehensive IT monitoring are a convenient additional benefit.
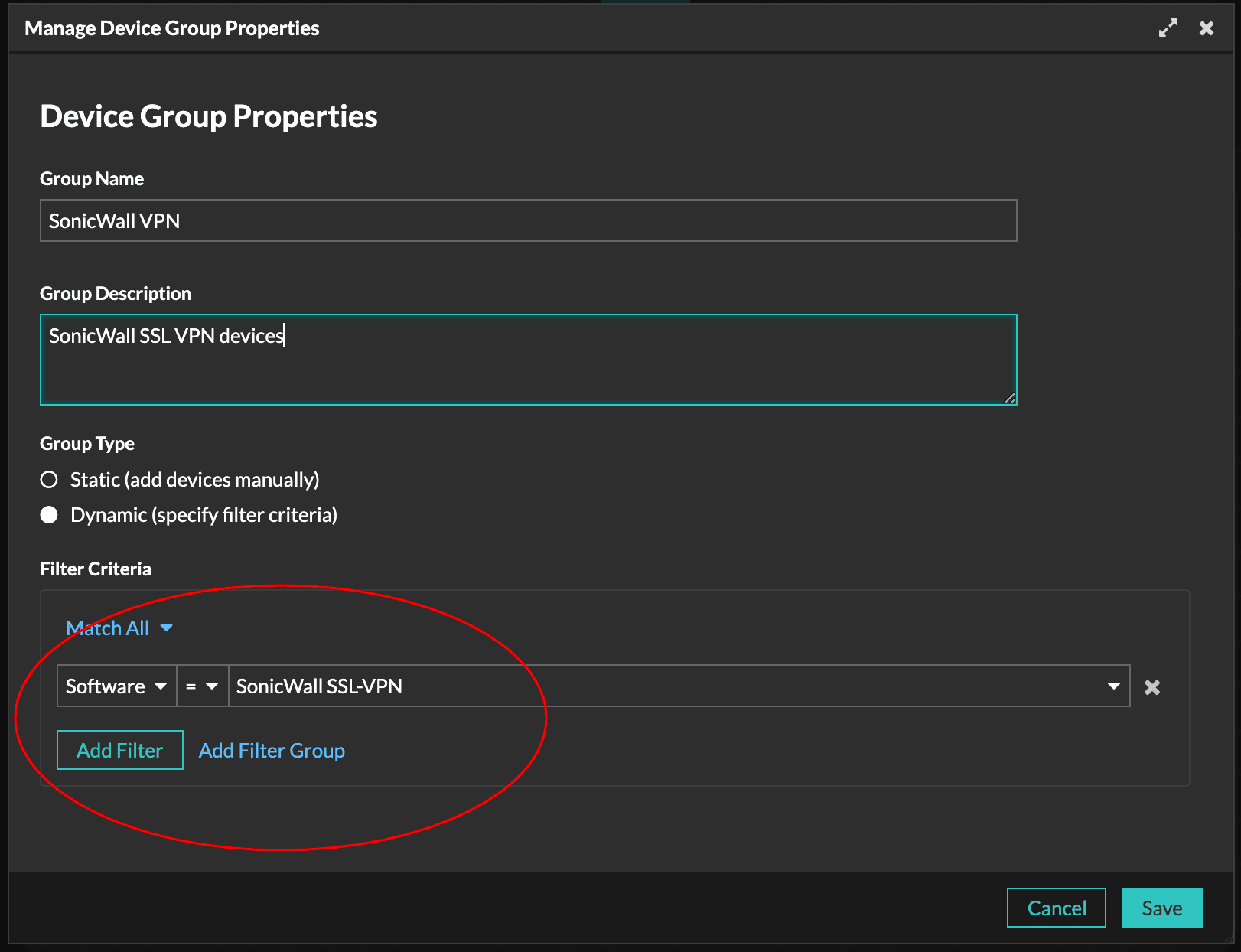
Using Reveal(x) to group and monitor affected SonicWall devices.
Inventory and Monitor Vulnerable Devices
ExtraHop customers can create a device grouping in order to closely monitor affected devices. Watch the video below for more detailed instructions.
- Click Assets on the top menu bar.
- Click Device Groups in the left menu.
- Click Create Device Group in upper right hand corner.
- Name the device group, then select Dynamic.
- In the Filter Criteria section, click Match All and then select SonicWall SSL-VPN from the drop-down list.
SolarWinds Serv-U Vulnerability
Another critical vulnerability, the SolarWinds Serv-U Memory Escape vulnerability (CVE-2021-35211) was announced this week. This vulnerability affects Serv-U version 15.2.3 which includes Serv-U Managed File Transfer Server and Serv-U Secured FTP. While the impact is believed to be limited to users of those services, the vulnerability is considered critical.
If exploited, the vulnerability would allow a remote attacker to run arbitrary code and take control of the affected system, enabling them to install and run programs and view or alter data. Microsoft has reported that this vulnerability is being actively exploited in highly targeted attacks.
In response, SolarWinds has released a patch, and Serv-U customers should immediately install updates to mitigate their risk and search for indicators of compromise. ExtraHop Reveal(x) customers can quickly identify affected devices by creating a device group for any device running Serv-U software. From there you can monitor devices for signs of compromise.
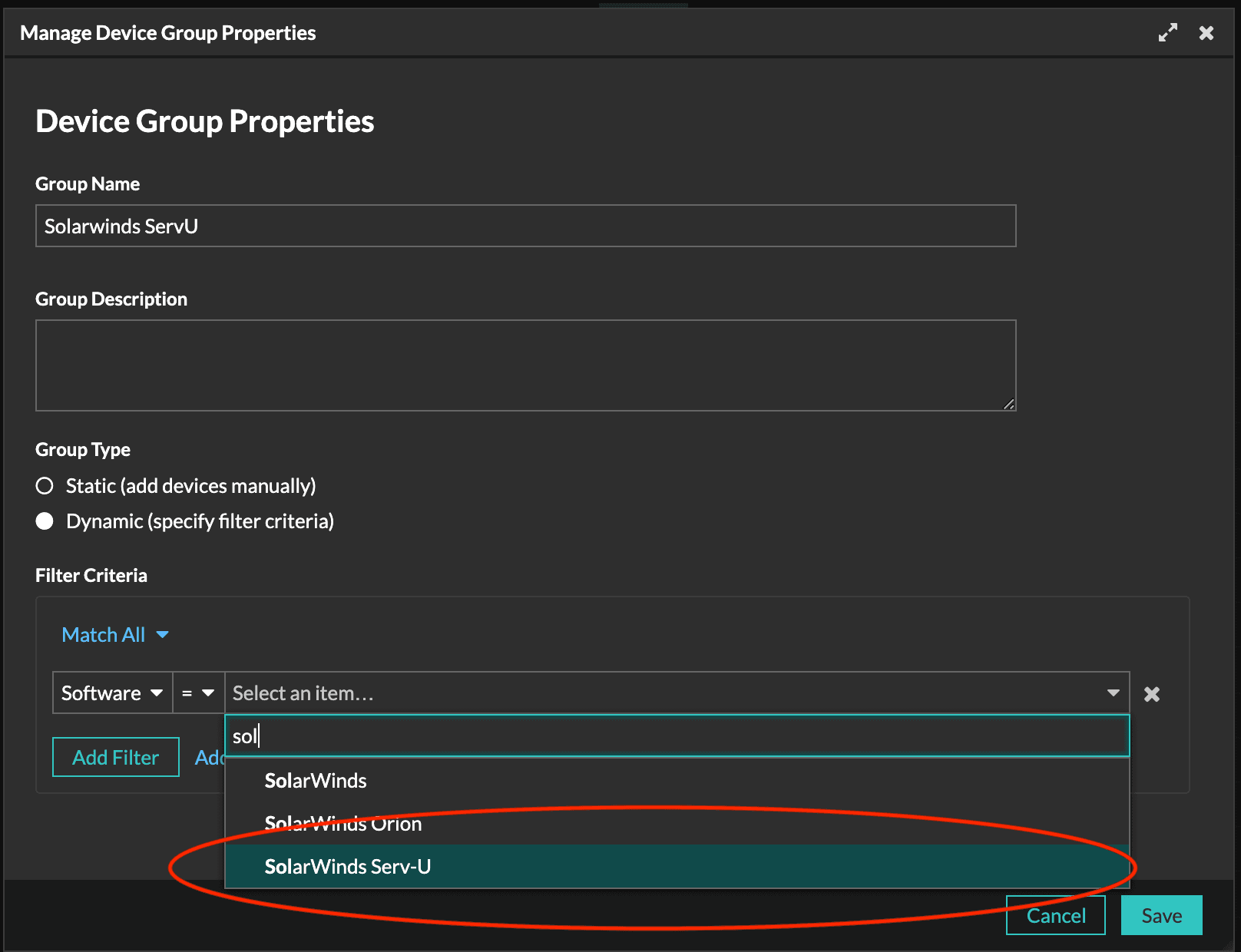
Create a device group to identify and monitor any device running the affected Serv-U software.
Want to test out Reveal(x) device inventory capabilities? Explore the full product in our open-access demo.

CISO
Jeff Costlow
Jeff Costlow is the CISO at ExtraHop. He started his career in computer security in 1997. Jeff has deep experience with networking protocols, a passion for secure software development and many years of software engineering under his belt.
In his spare time, Jeff enjoys building and sailing small boats, making beer or cider, mentoring for FIRST robotics, and raising Pacific Northwest mason bees.
Connect with Jeff on Twitter or LinkedIn!



